The Backbone of Digital Investigations
In today’s digital-first world, almost every crime leaves behind an online trail. From financial fraud to harassment, cyberstalking, and organized digital crime, communication has moved from voice calls and SMS to data-driven apps, encrypted chats, OTT platforms, and web-based services.
For investigators, this shift has changed one fundamental truth: Metadata is now more valuable than content.
Even when conversations are encrypted or routed through apps, the activity: logins, sessions, ports accessed, websites visited, and timestamps, still flows through the internet in the form of IP sessions.
This is where IPDR (Internet Protocol Detail Records) becomes one of the most important tools available to law enforcement.
IPDR doesn’t show what someone said or typed; instead, it shows what they did, when they did it, and from which device they did it, making it indispensable in uncovering digital patterns, identifying offenders, and reconstructing events in cybercrime cases.
Key Takeaways
- IPDR is one of the most powerful metadata sources for cybercrime investigations, more relevant today than CDR.
- It captures internet session logs, allowing investigators to map online actions with precise timestamps.
- IPDR helps in cases involving fraud, harassment, intrusion, child safety, and organized cybercrime.
- When correlated with CDR, CAF, device IDs, OSINT, and tower data, it builds a complete digital identity of suspects.
- Manual IPDR analysis is slow; AI-based platforms like Intelelinx drastically cut investigation time and improve accuracy.
- As digital crime evolves, IPDR has become indispensable for law enforcement, cyber cells, and intelligence agencies.
What is IPDR and Why It Matters in Cybercrime Cases
IPDR (Internet Protocol Detail Records) is metadata generated by ISPs that captures essential details about a user’s online session.

This includes:
- The IP address assigned to the user
- Websites or servers they connected to
- Ports and protocols used
- Start and end time of each session
- Data volume consumed
- Type of service or application
Think of IPDR as a high-level “activity log” of what a device was doing on the internet, without revealing message content.
How IPDR Differs From CDR
- CDR (Call Detail Records) logs voice call/SMS activity.
- IPDR logs internet activity and online behaviour.
In cybercrime cases, CDR shows “who called whom,” while IPDR shows “what online action happened and when.”
This makes IPDR far more potent in the modern investigation landscape, where nearly all illegal activity, from phishing and fraud to ransomware, happens over data channels.
How Law Enforcement Obtains and Uses IPDR
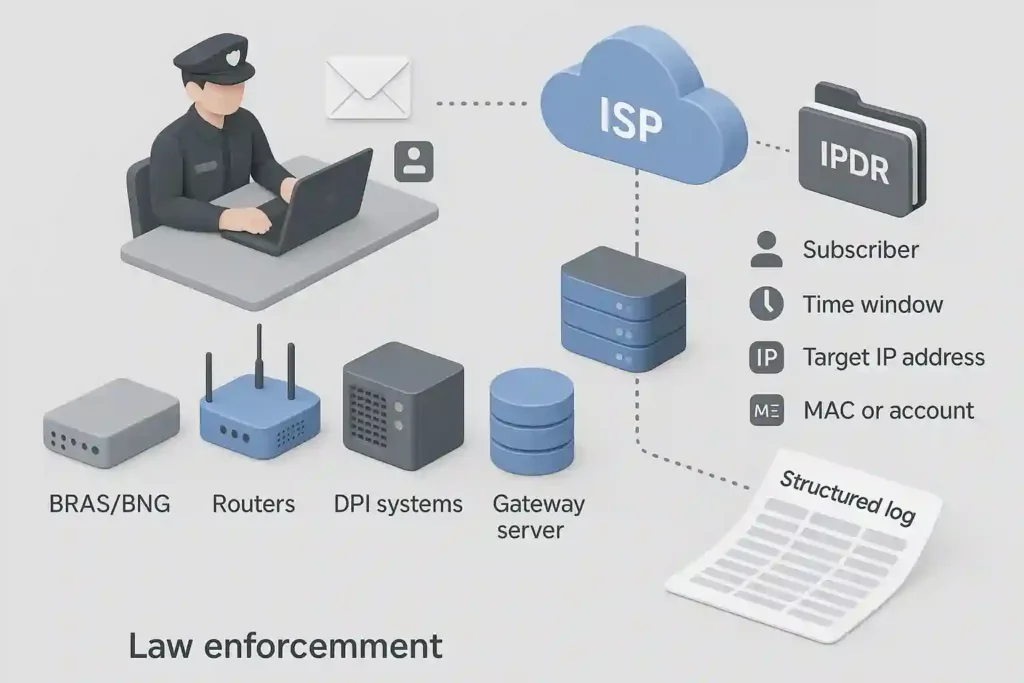
IPDR is generated and stored by ISPs through network elements such as:
- BRAS/BNG
- Routers
- DPI systems
- DHCP logs
- Gateway servers
When a request is initiated by a law enforcement agency as per legal process (with no country-specific compliance discussed here), the ISP retrieves the relevant IPDR logs tied to:
- A subscriber
- A specific time window
- A target IP address
- A device’s MAC or account information
Investigators then receive structured logs showing timestamped IP sessions, which they analyze to map behaviour and identify users behind suspicious or criminal activity.
Core Investigative Use Cases of IPDR in Cybercrime

IPDR is now used across almost every category of cyber investigation. Here are the most common, high-impact use cases:
Tracing Online Fraud & Scams
In cases involving digital fraud: phishing, OTP theft, online banking scams, e-commerce fraud, or mule accounts, IPDR helps investigators:
- Trace the origin of fraudulent login attempts
- Identify which websites or bank servers a device interacted with
- Establish timelines around suspicious transactions
- Pinpoint device behaviour around the time of the fraud
Example scenario: A fraudster logs into a victim’s banking portal. IPDR reveals the session connecting to the bank’s server at a precise timestamp, mapping it back to the suspect’s device or network.
Tracking Social Media Harassment, Stalking & Threats
Anonymous social media accounts are commonly used for:
- Online harassment
- Cyberstalking
- Threats or extortion
- Fake profiles for impersonation
IPDR allows law enforcement to:
- Map login sessions of anonymous accounts
- Identify the source IP behind posts or messages
- Link the activity to a specific subscriber or device
Even when social platforms don’t share content, session-level metadata forms strong investigative evidence.
Ransomware, Malware & Intrusion Investigations
Modern cyberattacks often rely on:
- Remote servers
- Command-and-control (C2) communication
- Unusual port activity
- VPN/proxy chains
- Foreign server connections
IPDR helps investigators detect and analyze:
- Outbound connections from infected devices
- Repeated communication to suspicious servers
- Connections over ports commonly used in intrusions
- Attempts to exfiltrate data
This helps identify infected hosts and trace attackers’ infrastructure.
Child Safety & Exploitation Investigations
This is one of the most critical areas where IPDR plays a role.
Investigators use IPDR to:
- Correlate timing of access to harmful content
- Link devices to accounts or websites visited
- Map behaviour across sessions
Since content itself may be encrypted or hosted abroad, IPDR’s timestamp correlation becomes a key investigative asset.
Mapping Organized Cybercrime Groups
From fraud rings to hacking groups, IPDR helps uncover:
- Communication patterns
- Shared devices or networks
- Timing overlaps
- Behavioural correlations between multiple actors
Combined with other datasets, investigators can reconstruct group structures, roles, and digital associations.
What Investigators Look for in IPDR Logs
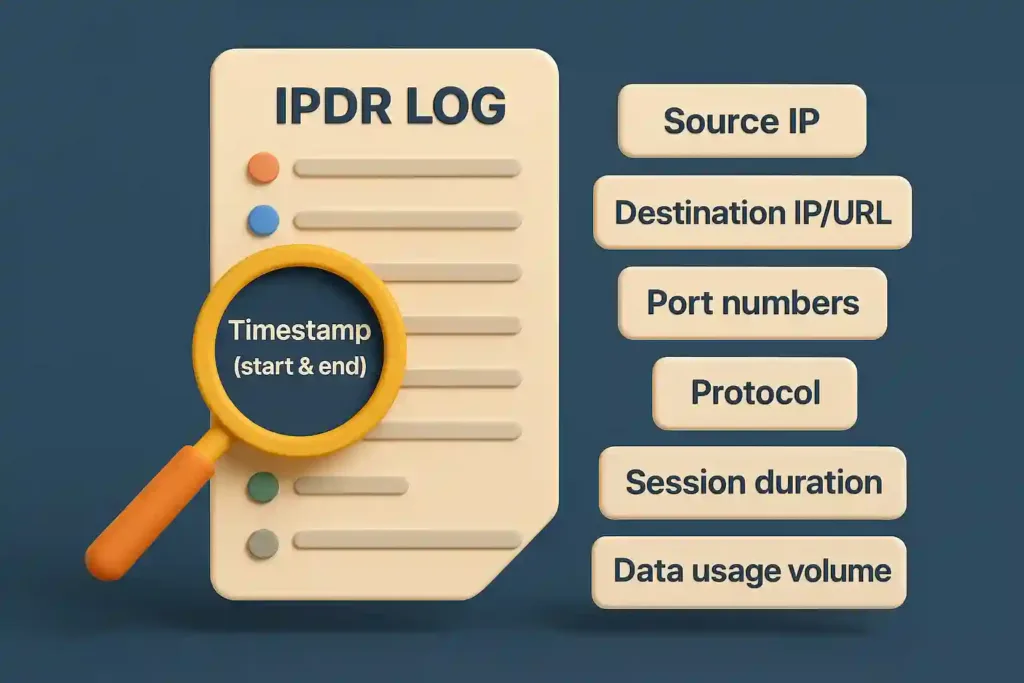
IPDR logs are rich in signals, if you know where to look. Investigators typically analyse:
Key Parameters
- Timestamp (start & end)
- Source IP (assigned to the suspect/subscriber)
- Destination IP/URL (websites, servers, apps)
- Port numbers (identifying type of service used)
- Protocol (HTTP, HTTPS, FTP, etc.)
- Session duration
- Data usage volume
Together, these parameters help reconstruct digital behaviour with minute precision.
Correlating IPDR With Other Datasets
IPDR alone provides strong insights, but its full power emerges when combined with other datasets.
Common Correlations Include:
- CDR → Link calls/SMS with online activity
- CAF → Validate subscriber identity
- Device identifiers → MAC, IMEI, host names
- Tower dumps → Validate movement and location
- WiFi logs → Narrow down physical presence
- OSINT → Match online behaviour with social media trails
- Video surveillance → Correlate physical presence with online activity
Successful investigations often depend on stitching these datasets together to map a complete digital identity.
The Need for Automated & AI-Based IPDR Analysis

Today’s investigations often span:
- Millions of records
- Hundreds of devices
- Dozens of digital personas
- Rapidly evolving threat structures
And analysts need answers fast.
Manual analysis of IPDR logs is slow, error-prone, and extremely resource-intensive. It can take days to correlate timestamps, patterns, and device behaviour.
Why AI-Based Analysis is Becoming Essential
- Instant correlation between IPDR, CDR, CAF, device IDs, OSINT
- Automated pattern recognition (suspicious behaviour, foreign access, C2 indicators)
- Timeline reconstruction for suspects
- Link analysis to visualize networks and connections
- Anomaly detection for unusual or risky activity
- Significant reduction in investigation time, from days to minutes
This is where next-generation analysis tools come in.
Introducing Innefu’s Intelelinx
Intelelinx is Innefu’s AI-powered CDR/IPDR investigation platform built for law enforcement, intelligence agencies, and cybercrime units.
It enables:
- Automated correlation of IPDR, CDR, CAF, OSINT, and device identifiers
- Visual link charts that show connections between suspects, devices, and patterns
- One-click timeline reconstruction
- Behavioural analytics to detect anomalies and hidden associations
- Faster evidence building through enriched metadata
Intelelinx is designed to give investigators clarity, speed, and precision, especially when dealing with complex cybercrime cases where every second matters.
Conclusion
IPDR is now one of the most powerful and reliable metadata sources in cybercrime investigations. Whether it’s cyber fraud, harassment, intrusion, or organized digital crime, IPDR helps law enforcement uncover the truth by mapping patterns, identifying devices, and reconstructing timelines.
But as cybercriminal activity grows in scale and complexity, manual log analysis is no longer enough.
Automated, AI-driven tools like Intelelinx enable investigators to make faster, more accurate decisions, turning raw metadata into actionable intelligence.
In a world where every crime has a digital footprint, IPDR remains one of the strongest pillars of modern digital investigations.
FAQ Section
What is IPDR in cybercrime investigation?
IPDR (Internet Protocol Detail Records) is metadata generated by ISPs that logs a user’s internet activity—such as websites visited, apps accessed, ports used, timestamps, and session duration. Law enforcement uses IPDR to trace digital footprints and reconstruct online behaviour during cybercrime investigations.
What is the full form of IPDR?
IPDR stands for Internet Protocol Detail Records.
It was standardized through industry bodies such as the IPDR Organization and TM Forum to help telecom operators maintain consistent internet session logs.
How is IPDR different from CDR?
- CDR (Call Detail Records) shows voice and SMS activity.
- IPDR (Internet Protocol Detail Records) shows internet session activity.
In modern cybercrime cases, where criminals use apps, OTT platforms, and anonymous accounts—IPDR provides far more investigative value.
What information does an IPDRcontain?
IPDR logs typically include:
- Source IP assigned to the user
- Destination IP / websites accessed
- Ports and protocols used
- Start and end timestamps
- Data uploaded and downloaded
- Session duration
This helps investigators identify behaviour patterns and map online activities.
How does law enforcement obtain IPDR records?
LEAs request IPDR from telecom/ISP providers through a legally approved process. The ISP then fetches logs for:
- A subscriber
- A specific time range
- A target IP or device
Investigators analyze these logs to trace activity and identify suspects.
What is IPDR used for?
IPDR is used for:
- Cyber fraud and financial scams
- Harassment and anonymous social media threats
- Ransomware and intrusion cases
- Child safety investigations
- Tracking organized cybercrime groups
- Telecom compliance and reporting
Can IPDR reveal the content of communication?
No. IPDR does not store message content.
It only logs session-level metadata, such as:
- When a device accessed a service
- What server or website it connected to
- Volume of data consumed
This metadata still provides strong investigative value.
Why is IPDR analysis often automated today?
Because investigators deal with:
- Millions of records
- Multiple devices
- Multiple apps and online identities
- Tight investigation timelines
AI-powered platforms (like Innefu’s Intelelinx) automate correlation across IPDR, CDR, CAF, OSINT, devices, and behaviour patterns—saving days of manual work.
Is IPDR useful even when communication apps are encrypted?
Yes. Even if content is encrypted, IPDR reveals:
- When the app was used
- From where
- For how long
- Which server it connected to
This helps investigators reconstruct timelines and correlate user behaviour with events.
Can IPDR help identify anonymous social media accounts?
Often, yes. Logs can show:
- Login sessions
- Access patterns
- Device activity matching behavior on specific platforms
This helps link anonymous accounts to real users or devices.




