Transform Defence Intelligence
with Non-Intrusive Ad-Intelligence
Covert Device Intelligence for National Security and Border Protection
Ad-Intelligence Platform
AdVisionary is a cutting-edge, ad-based intelligence platform that converts location data into actionable insights for national security. Using non-intrusive tracking via unique Ad-IDs, it delivers real-time geolocation intelligence across millions of devices. From detecting cross-border threats to identifying suspicious activity near critical infrastructure, AdVisionary empowers security teams with fast, privacy-first alerts—enabling rapid response and informed decisions in high-risk environments.
See it in Action
GeoSpatial Tracking & Analysis
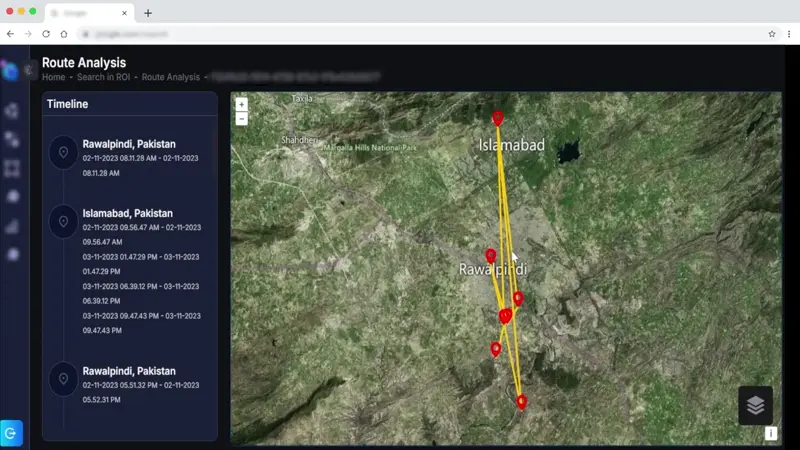
Monitor suspect movements in real time with integrated geolocation tools that provide precise tracking, route analysis, and hotspot detection for faster decision-making.
Intelligent Target Monitoring
Automatically flag high-risk activities and monitor targets across multiple data streams with AI-powered alerts, reducing manual workload and response times.
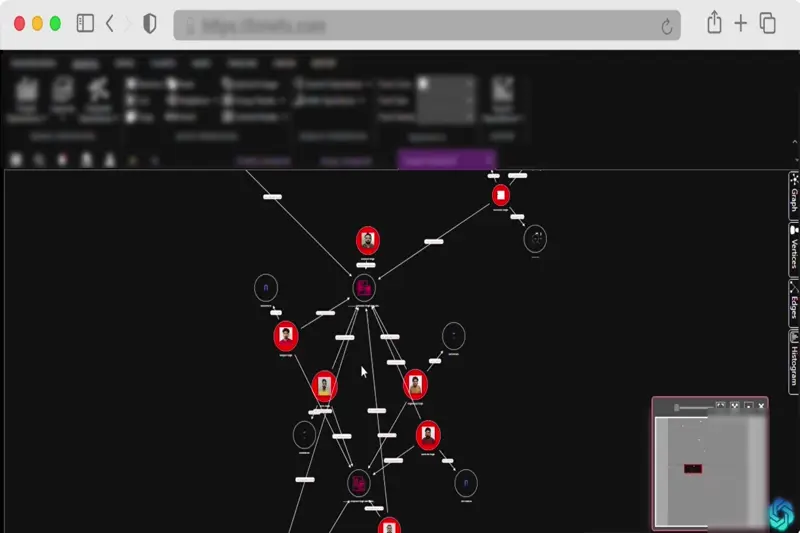
Link Analysis
The system helps find connections between different people, like discovering gang members or criminal networks by looking at relationships in the dossiers
Core Capabilities of AdVisionary
Cross-Border Intelligence
Track device movements between countries by leveraging ad network data that flows freely across international boundaries, providing visibility where traditional surveillance methods cannot reach.
Real-Time Alert System
Receive instant notifications when monitored devices enter or leave specified areas of interest, allowing immediate tactical response to emerging situations.

Advanced Demographic Profiling
Build comprehensive intelligence profiles based on device usage patterns, installed applications, and location data to identify suspicious behavior and potential security threats.
Path and Route Analysis
Map movement patterns with precision, including frequency and duration of stays in critical areas, to establish behavioral baselines and identify suspicious deviations.
Powerful Security Features
Real World Use Cases

Criminal Investigations
Track suspect movements and communication patterns across time and location, establishing critical timelines and meeting points to build compelling cases.
Cross-Border Monitoring
Security agencies need to track movements of individuals or groups across borders, such as terrorists moving from Pakistan to India.
Protecting Critical Infrastructure
Monitoring and safeguarding vital installations like troop camps and other sensitive locations from potential threats.
Monitor Adversary Buildup
Detecting and monitoring shifts in defence unit locations and identifying potential security breaches.