In a world where cyberattacks are becoming more automated, more intelligent, and more frequent, organizations can no longer rely on passwords alone. A stolen credential today can unlock emails, internal systems, cloud platforms, VPNs, and even mission-critical government or defence applications. This is why Multi-Factor Authentication (MFA) has emerged as one of the most critical pillars of cybersecurity in 2025.
MFA ensures that even if one factor is compromised, attackers still cannot gain access. And with identity becoming the most targeted attack surface, organizations across defence, BFSI, healthcare, telecom, and enterprises are adopting MFA faster than ever before.
What Exactly Is Multi-Factor Authentication?
Multi-factor authentication is a security process where users verify their identity using more than one credential. Instead of depending only on passwords, which are often weak, reused, or stolen, MFA adds independent layers of verification.
Authentication factors are usually classified into three types:
- Something you know (password, PIN)
- Something you have (mobile device, hardware token)
- Something you are (fingerprint, facial scan)
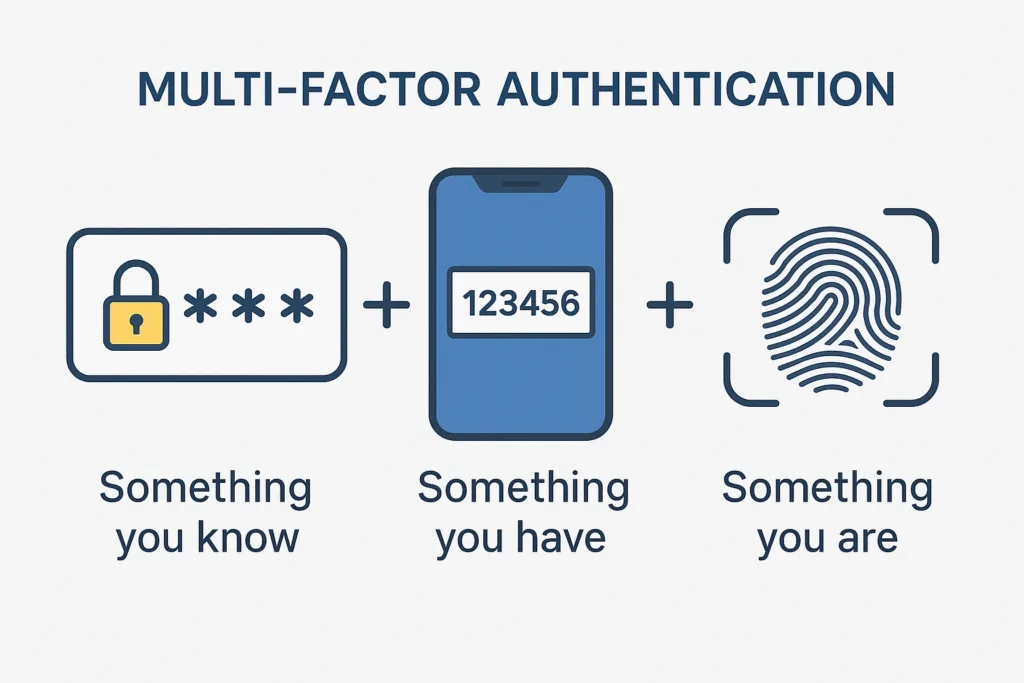
By combining two or more of these, MFA makes unauthorized access significantly harder, even for sophisticated attackers.
Why MFA Has Become a Cybersecurity Priority
The digital environment has evolved rapidly. Remote work, mobile access, and cloud adoption have made identities accessible from anywhere. At the same time, cybercriminals have become more creative, often using phishing-as-a-service kits, stolen databases, and automated bots to break into systems.
A single leaked password today could compromise an entire organization.
Governments are also tightening regulations, requiring MFA for critical infrastructure, financial systems, telecom networks, and sensitive citizen data. For defence and intelligence agencies, identity-based attacks pose national security risks, making MFA indispensable.
Simply put, MFA has become the first and most important checkpoint of digital trust.
How MFA Works Behind the Scenes
When a user tries to log in, the system verifies multiple factors before granting access. For example, the user may enter a password and then approve a push notification on their mobile device. Or they may log in with their fingerprint and then validate with a time-based one-time password (TOTP).
Modern platforms often include adaptive authentication, which analyzes the risk of the login attempt—location, behavior, device, and access time. If something looks unusual, the system automatically asks for an additional verification factor.
This makes MFA not only secure but intelligent.
Different Forms of Multi-Factor Authentication
MFA has evolved far beyond traditional OTP-based systems. Today, organizations choose authentication methods based on their risk profile and user workflow.
- Biometric authentication—fingerprints, face recognition, iris scan is widely considered the most powerful form of identity verification due to its uniqueness and convenience.
- Authenticator apps such as TOTP-based tokens offer a secure alternative when network connectivity is unreliable.
- Push-based authentication, where users tap “Approve” on their device, provides a frictionless and phishing-resistant login experience.
- For high-security environments, hardware tokens with cryptographic keys provide maximum protection.
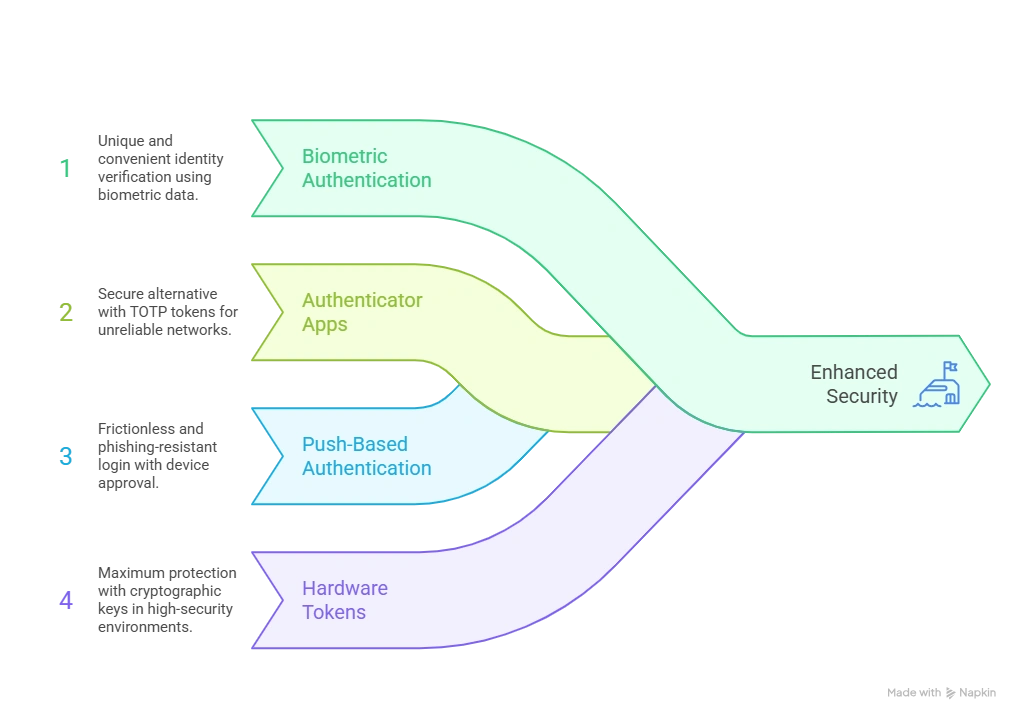
The flexibility of MFA ensures that every organization can design a model that fits its needs.
Why MFA Is Critical for Government, Defence & Law Enforcement
Sensitive agencies face some of the world’s most advanced adversaries. Attackers aim to steal privileged identities, infiltrate classified systems, or exfiltrate national security data. MFA significantly strengthens identity assurance by requiring verified presence for every login attempt.
Government agencies, police forces, intelligence teams, defence personnel, and federal institutions increasingly rely on biometrics, tokens, and PKI-based authentication to safeguard mission-critical systems. In environments where even a single unauthorized login can lead to catastrophic outcomes, MFA has become non-negotiable.
MFA Inside a Zero Trust Model
Zero Trust security is built on a simple principle: never trust any user or device by default.
MFA is one of the core enforcers of Zero Trust. It ensures that every access request, no matter who or from where, must be verified continuously. Even after login, if the system detects unusual behavior or risk, MFA can be re-triggered automatically.
This dynamic verification aligns perfectly with modern hybrid environments where people work across networks, devices, and locations.
Challenges with MFA (And How Modern Systems Solve Them)
Some organizations hesitate to adopt MFA due to concerns about user experience or legacy application integration. Traditional OTP-based systems can sometimes be slow or inconvenient, and older applications may not support modern authentication protocols.
Fortunately, modern MFA platforms use innovations like:
- Push notifications instead of SMS
- Biometric verification for faster access
- Deep Packet Inspection (DPI) to secure legacy protocols
- Mobile-based tokens to eliminate hardware costs
- Adaptive authentication to reduce friction
With the right technology, MFA can be deployed smoothly across even the most complex environments.
Introducing AuthShield: Innefu’s Unified MFA Platform
AuthShield is Innefu’s enterprise-grade authentication platform built to meet the security challenges of modern organizations. Designed to protect everything from cloud applications to legacy email systems, it brings all authentication methods under one secure, unified umbrella. AuthShield strengthens cybersecurity with advanced multi-factor authentication while ensuring a seamless, frictionless user experience.
The platform supports biometric authentication, mobile tokens, push notifications, facial recognition, VPN access security, and cloud identity protection. Whether an organization needs to secure government applications, enterprise email systems, or financial transaction platforms, AuthShield adapts to every environment with ease.
One of its most differentiated capabilities is its Deep Packet Inspection (DPI) engine. This allows AuthShield to integrate with legacy systems using older protocols such as POP3 and IMAP, providing strong authentication even where modern identity systems usually fail. This ensures organizations do not need costly upgrades to secure older systems.
AuthShield offers fingerprint biometric verification, PKI-backed one-touch login, mobile-based token generation, facial recognition, and desktop-based TOTP authentication. Its versatility makes it ideal for BFSI, healthcare, telecom, defence, intelligence agencies, and large enterprises. No matter the industry, AuthShield enhances protection, simplifies authentication workflows, and maintains a consistent, Zero Trust-aligned security posture.
Best Practices for Deploying MFA Effectively
Organizations should begin with high-risk users such as administrators, SOC teams, finance personnel, or defence operators. Integrating MFA with IAM and SSO helps unify identity management and reduce user friction. Adaptive authentication should be implemented so that the system adjusts verification requirements based on risk.
Legacy applications must also be included in the rollout. Platforms like AuthShield make this possible without disruption. Continuous monitoring and periodic testing ensure that authentication remains strong and aligned with evolving cyber threats.
What the Future of MFA Looks Like
Over the next few years, MFA will move towards passwordless authentication driven by biometrics, cryptographic devices, and decentralized identity models. Behavioral biometrics will enable continuous, invisible authentication that works in the background. AI-powered identity signals will determine risk in real-time, making authentication both seamless and secure.
The future is not just MFA—it’s continuous, intelligent identity assurance.
Conclusion
Cybersecurity starts with identity, and identity security starts with Multi-Factor Authentication. MFA is no longer an add-on; it is the foundation of modern defence strategies. With threats growing more sophisticated, organizations must strengthen authentication with multiple, independent verification layers.
Solutions like Innefu’s AuthShield make MFA not just stronger, but smarter. By integrating biometrics, push-based authentication, mobile tokens, and DPI-powered legacy security, AuthShield delivers enterprise-grade protection that secures every corner of your digital ecosystem.
To explore how AuthShield can protect your organization, schedule a demo and take the next step toward Zero Trust security.




