Why Cyber Forensics Matters Today
In 2024 alone, the world saw some of the most sophisticated cyberattacks ever recorded, ransomware crippling hospitals, phishing campaigns targeting government agencies, and financial fraud rings operating across multiple continents. Each of these incidents left behind one vital element: digital evidence.
This is where cyber forensics steps in. Often described as the “CSI of the digital world,” it is the science of uncovering, preserving, and analyzing digital evidence to understand how an attack happened, who was behind it, and how future incidents can be prevented. It’s not just about retrieving deleted files or tracing IP addresses; it’s about reconstructing the entire digital crime scene.
For years, organizations treated forensics as purely reactionary, something to do after an incident. But with the rising complexity of threats, that approach is no longer enough. Today, cyber forensics is also proactive: it powers cybercrime investigation, helps analysts predict emerging threats, and strengthens security operations by feeding insights back into defence systems.
In essence, cyber forensics and digital forensics are no longer niche disciplines. They are now core pillars of modern cybersecurity, law enforcement, and even national security, enabling investigators to connect the dots faster, bring criminals to justice, and ensure that no digital footprint goes unnoticed.
What is Cyber Forensics?

At its core, cyber forensics (sometimes used interchangeably with digital forensics) is the discipline of collecting, analyzing, and preserving data from computers, mobile devices, networks, and cloud environments to uncover the truth about a cyber incident.
Think of it as a digital detective’s toolkit: when a cyberattack or online crime occurs, the specialists retrace every step of the intruder: how they gained access, what systems they touched, what data they stole, and how they covered their tracks.
Unlike routine IT monitoring or cybersecurity, which focus on prevention and defence, cyber forensics focuses on investigation and evidence. The evidence collected must be:
- Accurate – capturing the digital trail without altering it.
- Preservable – so it can be presented in courts of law.
- Actionable – so law enforcement, regulators, or corporate security teams can act on it.
Cyber forensics spans both criminal investigations (such as tracking cyber fraud, child exploitation, or hacking cases) and corporate/defence investigations (like insider threats, intellectual property theft, or nation-state attacks).
In other words, cyber forensics is more than data recovery. It is about contextual intelligence, piecing together the who, what, when, and how of a digital event, and ensuring that justice and security are backed by hard, irrefutable evidence.
What Does Cyber Forensics Do?
Cyber forensics goes beyond uncovering a “digital footprint.” It provides clarity, accountability, and evidence in environments where data is often complex, fast-moving, and deliberately manipulated by adversaries.
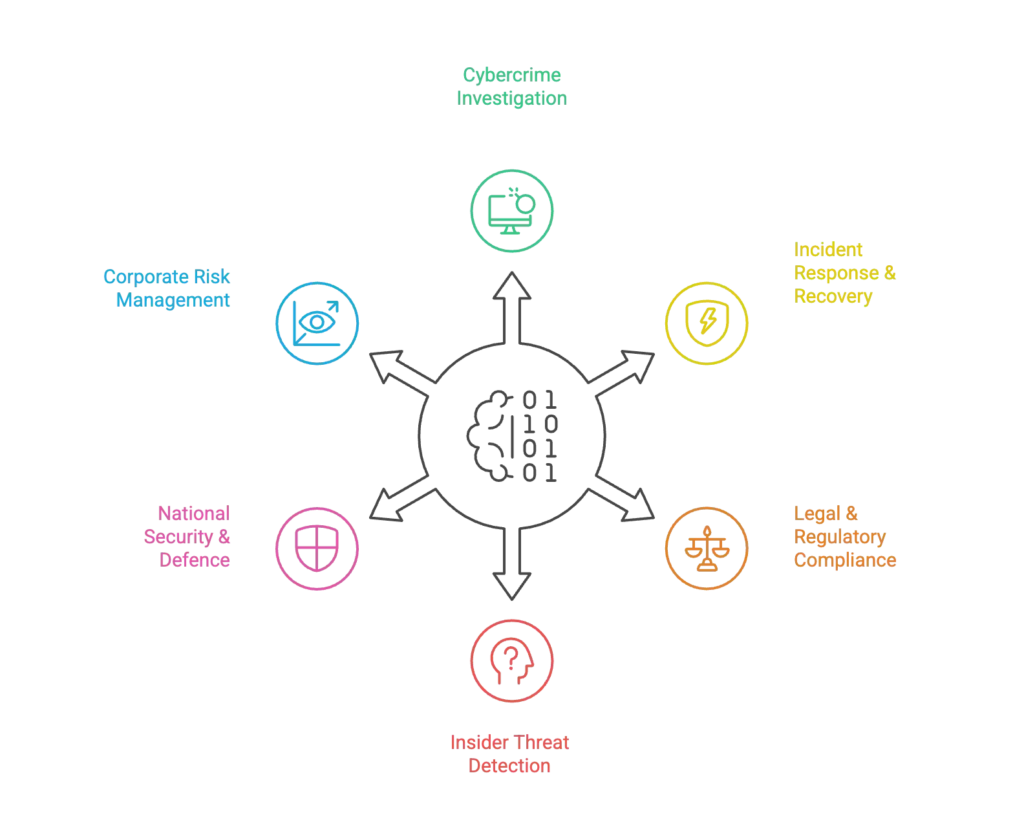
Here are the key roles cyber forensics plays today:
Cybercrime Investigation
From phishing scams and ransomware attacks to online fraud, cyber forensics specialists analyze compromised systems, emails, and digital wallets to trace perpetrators.
Example: Following the Bitcoin trail of a ransomware payment to uncover the criminal group behind it.
Incident Response & Recovery
After a cyberattack, forensics helps determine how attackers got in, what they did, and how to contain the damage. This ensures systems are restored safely without leaving backdoors open.
Legal & Regulatory Compliance
It provides court-admissible evidence. Whether it’s a corporate data breach or insider trading case, forensic reports become part of official investigations.
Insider Threat Detection
Not all threats come from outside. Forensic analysis of employee devices, access logs, and emails can expose unauthorized data exfiltration or misuse of credentials.
National Security & Defence
In the defence domain, cyber forensics supports counter-espionage, military intelligence, and cyber warfare investigations by uncovering adversary tactics and malware signatures.
Corporate Risk Management
Companies use forensic insights to strengthen security policies and prevent repeat attacks. Forensics doesn’t just solve a crime; it teaches organisations how to avoid it in the future.
In short, cyber forensics does three things simultaneously: it investigates the past (what happened), secures the present (containment), and protects the future (prevention).
Cyber Forensics vs Digital Forensics – What’s the Difference?

In everyday conversations, people often blur the line between digital forensics and cyber forensics. While they are closely related, there are important distinctions:
Digital Forensics: The Bigger Umbrella
- Covers the collection, preservation, and analysis of all digital evidence across any device.
- Includes computers, hard drives, mobile devices, IoT gadgets, cloud storage, and more.
- Goal: Retrieve and validate digital evidence, regardless of whether the crime is “cyber” in nature or not.
👉 Example: Investigating deleted files on a suspect’s laptop in a fraud case.
Cyber Forensics: The Internet-Focused Subset
- A specialized branch within digital forensics.
- Focuses specifically on networks, online systems, and cybercrimes.
- Deals with malware tracing, phishing, ransomware, DDoS attacks, unauthorized network access, and darknet investigations.
👉 Example: Tracing how a hacker remotely accessed that same laptop to plant ransomware.
A Simple Analogy
Think of digital forensics as the whole library of digital evidence.
Cyber forensics is the dedicated section within that library that deals only with internet-based attacks and crimes.
Types of Cyber Forensics
Cyber forensics is not a single discipline, it’s a collection of specialized practices that deal with different sources of digital evidence.

Here are the key types:
Network Forensics
- Focus: Monitoring and analyzing network traffic to detect intrusions, data exfiltration, or unauthorized access.
- Tools and techniques include packet sniffing, intrusion detection logs, and reconstructing attack paths.
- Example: Tracing a ransomware attack back to the command-and-control server used by attackers.
Malware Forensics
- Focus: Studying malicious code such as viruses, worms, trojans, or ransomware to understand its behavior and origin.
- Analysts reverse-engineer binaries, examine payloads, and track signatures.
- Example: Determining whether a malware sample was designed for espionage or financial theft.
Email & Communication Forensics
- Focus: Analyzing emails, messaging apps, and VoIP calls for traces of phishing, fraud, or insider threats.
- Helps authenticate headers, timestamps, and routing paths.
- Example: Uncovering a phishing campaign targeting employees of a defence contractor.
Mobile Device Forensics
- Focus: Extracting and analyzing evidence from smartphones, tablets, and IoT devices.
- Includes call data records (CDR), GPS logs, app data, deleted messages, and multimedia.
- Example: Recovering WhatsApp chats and GPS history in a criminal investigation.
Cloud Forensics
- Focus: Investigating evidence stored in cloud environments (AWS, Azure, Google Cloud, private clouds).
- Challenges include shared infrastructure, encryption, and jurisdictional issues.
- Example: Identifying an insider who leaked sensitive documents to a personal cloud storage account.
Web & Database Forensics
- Focus: Examining web applications, databases, and online services.
- Tracks SQL injections, unauthorized admin access, and suspicious log entries.
- Example: Proving that a breach occurred through a web application vulnerability.
Memory & System Forensics
- Focus: Analyzing RAM dumps, registries, and OS logs to uncover live attack traces.
- Useful in detecting fileless malware and volatile evidence that disappears after shutdown.
- Example: Capturing the memory of a compromised server to trace ongoing rootkit activity.
Cyber Forensics and Information Security – The Connection

At first glance, cyber forensics may sound like a post-mortem discipline, something that comes into play after a cyberattack. But in reality, cyber forensics and information security are tightly connected and mutually reinforcing.
From Reactive to Proactive
- Traditional information security focuses on prevention – firewalls, intrusion detection, encryption.
- It adds the ability to investigate, trace, and learn from breaches, turning past incidents into actionable security improvements.
- Example: If malware is detected in an enterprise, forensic analysis of how it entered helps patch the vulnerability and prevent recurrence.
Compliance and Legal Requirements
- Many industries like finance, defence, telecom require not just protection, but proof of how incidents were handled.
- Cyber forensics provides the chain of custody, audit trails, and digital evidence needed for regulatory compliance.
- Example: A financial institution hit by fraud can show regulators exactly how the attack occurred and what steps were taken to mitigate it.
Enhancing Threat Hunting and Detection
- By combining forensic insights with threat intelligence feeds, organizations can predict and identify attack patterns before they strike again.
- Forensics provides the “why and how” behind attacks, while information security provides the “shield”.
- Together, they enable advanced threat hunting software and real-time cyber incident response tools.
National Security Implications
- In defence and law enforcement, the link is even stronger.
- Cyber forensics ensures adversaries’ digital footprints, from espionage campaigns to terror financing networks, are preserved and acted upon.
- Information security then hardens systems against repeat attempts, closing the loop.
Tools and Techniques in Cyber Forensics
Cyber forensics relies on a mix of specialized tools and investigative techniques to collect, preserve, and analyze digital evidence. These tools must be accurate, tamper-proof, and court-admissible, while also supporting the scale of modern cyber investigations.
Forensic Imaging and Case Management
- The first step in any cyber forensic investigation is to capture a bit-by-bit copy (forensic image) of storage media or devices.
- Once evidence is secured, forensic case management software ensures proper documentation, chain of custody, and streamlined reporting.
- Innefu’s RapiDFIR offers investigators an integrated platform for managing digital evidence, automating documentation, and ensuring courtroom-ready reports.
Log Analysis and Network Forensics
- Investigators analyze system logs, firewall logs, and intrusion detection alerts to reconstruct how an attack occurred.
- Advanced forensic analysis software correlates these logs with external threat intelligence for faster attribution.
- This is where threat hunting software and cyber incident response tools come into play, enabling rapid containment.
Link Analysis and Communication Mapping
- Cyberattacks often involve networks of accounts, servers, or actors rather than isolated incidents.
- Link analysis software helps visualize these relationships, exposing hidden connections between seemingly unrelated digital entities.
- Innefu’s Intelelinx provides robust call data record (CDR) analysis and communication mapping, crucial for both cybercrime and cross-border investigations.
OSINT Integration
- Open-source intelligence (OSINT) is increasingly vital in cyber forensics. Social media activity, dark web chatter, or leaked credentials often reveal attacker intent or affiliations.
- Platforms like Innsight (Innefu’s OSINT solution) integrate OSINT into forensic workflows, enabling investigators to correlate external signals with internal breaches.
AI-Powered Forensics
- AI is transforming cyber forensics by automating anomaly detection, video analysis, and natural language processing.
- For example, AI-driven video analytics can identify patterns in surveillance footage related to cyber-physical intrusions, while speech-to-text tools transcribe intercepted audio for faster review.
- Innefu’s AI Vision supports this capability by enhancing real-time forensic video and image analysis.
Conclusion – Cyber Forensics as a Strategic Imperative
Cyber forensics is no longer a niche technical field; it’s a strategic pillar of modern security and justice systems. Whether it’s dismantling ransomware networks, attributing state-sponsored cyber intrusions, or prosecuting financial fraud, cyber forensics ensures that digital evidence is collected, preserved, and analyzed with accuracy and credibility.
By combining forensic analysis software, link analysis, OSINT integration, and AI-driven insights, agencies can transform investigations from reactive exercises into proactive, intelligence-led operations.
As threats evolve, the agencies that succeed will be those that treat cyber forensics as both science and strategy, building institutional memory, enabling predictive threat detection, and ensuring no digital trace goes unnoticed.
FAQs on Cyber Forensics
Q1. What is cyber forensics?
It is the practice of collecting, analyzing, and preserving digital evidence from computers, networks, and online activity to investigate cybercrimes such as hacking, fraud, and identity theft.
Q2. What does cyber forensics do in practice?
It helps investigators uncover how a cyberattack happened, identify the perpetrators, and provide court-admissible evidence. It also supports proactive monitoring and threat hunting.
Q3. What are the different types of cyber forensics?
- Computer forensics – analyzing desktops, laptops, servers.
- Network forensics – monitoring and investigating data packets and logs.
- Mobile forensics – extracting evidence from smartphones and tablets.
- Cloud forensics – securing data from cloud platforms.
- Malware forensics – dissecting malicious code to understand attack vectors.
Q4. What is the difference between cyber forensics and digital forensics?
- Digital forensics is the broader umbrella, covering all digital devices and media.
- Cyber forensics is a subset, focusing specifically on internet-based crimes, networks, and online data.
Q5. How does cyber forensics support national security?
By combining cyber incident response tools, forensic case management, and intelligence fusion, it helps governments detect espionage, prevent cyber-terrorism, and secure critical infrastructure.
Q6. What tools are used in cyber forensics?
Tools include forensic imaging software, link analysis tools, OSINT platforms, and AI-powered forensic analysis software. These ensure evidence integrity, faster analysis, and actionable insights.




