Why Monitoring Is the Financial System’s Watchtower
In 2023, U.S. regulators fined a major global bank over $400 million for failing to detect suspicious activity tied to organized crime. The transactions weren’t unusual at first glance – wire transfers, small deposits, cross-border payments. But when pieced together, they revealed a layering scheme worth billions.
What went wrong? The bank’s transaction monitoring system was outdated, overly rule-based, and unable to adapt to evolving laundering typologies.
This case highlights why Anti-Money Laundering (AML) transaction monitoring is more than just compliance. It is the frontline of financial crime defence, protecting institutions from reputational damage, regulatory fines, and most importantly – from being conduits of terrorism financing, drug cartels, and cybercrime.
This guide breaks down how AML transaction monitoring works, why it’s so critical in 2025, and how AI-driven tools like Prophecy Eagle I are transforming monitoring into true financial intelligence.
Key Takeaways
- AML transaction monitoring continuously scans customer activity to detect suspicious behavior.
- It combines rule-based scenarios, behavioral analytics, and machine learning.
- False positives are the biggest challenge, but AI and link analysis improve precision.
- Modern AML monitoring is not just compliance, it’s national security.
- Platforms like Innefu’s Prophecy Eagle I move monitoring from detection to intelligence.
What is AML Transaction Monitoring?

At its core, AML transaction monitoring is the process by which financial institutions, fintechs, and regulators track financial activity in real time (or near-real time) to detect and prevent illicit money flows.
It is not about spotting one-off unusual events, but rather about identifying suspicious patterns over time that may indicate money laundering, terrorism financing, or fraud.
How AML Transaction Monitoring Works: A Step-by-Step Breakdown
Below is the end-to-end flow most mature programmes follow. You can map each step to your current stack and quickly see where gaps exist.
1) Ingestion: Pull transactions from every channel
Sources: core banking, cards, wallets, wire/ACH/RTGS, trade finance, remittance, crypto gateways, insurance payouts, merchants/PSPs.
Modes: real time (streaming) for instant alerts; batch for end-of-day backfills and historical lookbacks.
Tip: include failed/declined attempts and reversals, launderers “probe” thresholds first.
2) Normalisation & Data Quality
Standardise field names, currencies, timestamps, and counterparty formats.
De-duplicate and handle missing values (e.g., null beneficiary address).
Geo-resolve IPs and locations; harmonise free-text (beneficiary names, purposes).
Why it matters: poor data quality is the #1 driver of false positives and missed links.
3) Enrichment (make raw events investigative)
KYC/CDD profile: risk rating, occupation/NAICS, residency, expected activity.
Watchlists & sanctions: UN/OFAC/EU, domestic lists, adverse media.
PEP/Relatives & Close Associates (RCA) flags.
Device & channel fingerprints, login metadata, branch/agent IDs.
Network context: historical counterparties, shared addresses, shared directors.
4) Customer Risk Segmentation
Assign baseline risk (low/medium/high, or a continuous score) using CDD, geography, product, and behaviour.
Drive scenario sensitivity from segment (e.g., tighter thresholds for high-risk offshore corporates).
5) Scenario/Rules Engine (deterministic controls)
Typical scenarios:
Thresholding/structuring: multiple sub-threshold cash deposits within a rolling window.
Velocity spikes: unusual burst of wires/new beneficiaries in 24–72 hours.
Jurisdiction risk: transfers to/from high-risk or sanctioned corridors.
Product misuse: trade finance discrepancies (over/under-invoicing patterns), prepaid cards used as “cash mules”.
Crypto touchpoints: fiat–crypto–fiat loops with mixers/tumblers in path.
Good programmes maintain a versioned scenario library with business justifications and testing evidence.
6) Behavioural Analytics (profile vs present)
Build customer-level baselines: typical amounts, frequency, counterparties, geographies.
Alert when current activity deviates materially from the customer’s norm and peer cohort (e.g., SMEs in the same industry).
Benefits: major reduction in “legitimate but large” alerts that rules alone over-flag.
7) Machine Learning Models (adaptive detection)
Supervised models: learn from labelled cases (true positives/false positives) to rank alert likelihood.
Unsupervised models: cluster and spot anomalies without labels (useful for emerging typologies).
Graph analytics: detect layering patterns, circular flows, hub-and-spoke shells, rapid multi-hop transfers.
Model governance: document features, training data, stability tests, and explainability (LIME/SHAP or rule surrogates).
8) Entity Resolution (who is who, really?)
Merge fragmented identities across systems: name variants, transliteration, shared phones/emails, common directors/UBOs.
Create golden entities (persons/orgs/devices/accounts) to avoid “alerting by alias”.
Critical for exposing synthetic IDs and duplicate customer records.
9) Link Analysis & Network Views
Build transaction graphs over lookback windows (e.g., 90/180/365 days).
Surface hidden associations (shared addresses/IPs, common beneficiaries).
Identify money mule networks and shell clusters reused across time.
Provide investigator-ready visuals (node-link maps, timelines, geo trails).
10) Alert Generation & Smart Triage
Scoring & prioritisation: combine rule hits, ML scores, entity/network risk, sanctions proximity.
De-dup & clustering: group related alerts into a single case to reduce noise.
Work queues: route by product expertise, language, or jurisdiction.
11) Investigation Workflow (Case Management)
One workspace with transactions, KYC, watchlist results, network view, notes, attachments.
Checklists/playbooks tied to scenario type (cash structuring vs TBML vs crypto).
Collaboration & hand-offs with time-stamped audit trails.
Outcome codes: Closed-No Issue, SAR/STR Filed, Monitor, Escalate to FIU/law enforcement.
12) Regulatory Reporting & Evidence Packaging
Auto-populate SAR/STR forms with narrative templates, key transactions, counterparties, timelines, and rationale.
Maintain defensible records: data lineage, scenario version, analyst actions, due dates, acknowledgments.
13) Feedback Loop (continuous improvement)
Feed dispositions (TP/FP) back into rules thresholds and ML training sets.
Retire low-value scenarios; A/B test new logic on shadow data before going live.
Track precision/recall, alert volume, time-to-close, and SAR conversion rates.
14) Controls: Explainability, Auditability, Compliance
Model explainability for auditors and regulators; keep model risk management documentation current.
Access controls & segregation of duties (maker–checker).
Data retention & privacy obeying local laws (GDPR/DPDP, etc.).
Stress tests for high-volume days and crisis scenarios.
15) Deployment Architectures
Real-time streaming for immediate interdiction; batch analytics for deep lookbacks.
On-prem/air-gapped options for sensitive environments; hybrid with privacy-preserving controls.
LLM assistants (on-prem) for summarising cases and answering natural-language queries (e.g., “Show all links from Acct X to any PEP via three hops in 180 days”).
Techniques Used in AML Transaction Monitoring
Transaction monitoring is not a single method, it’s a layered defence. Different techniques work together to balance coverage, accuracy, and efficiency.
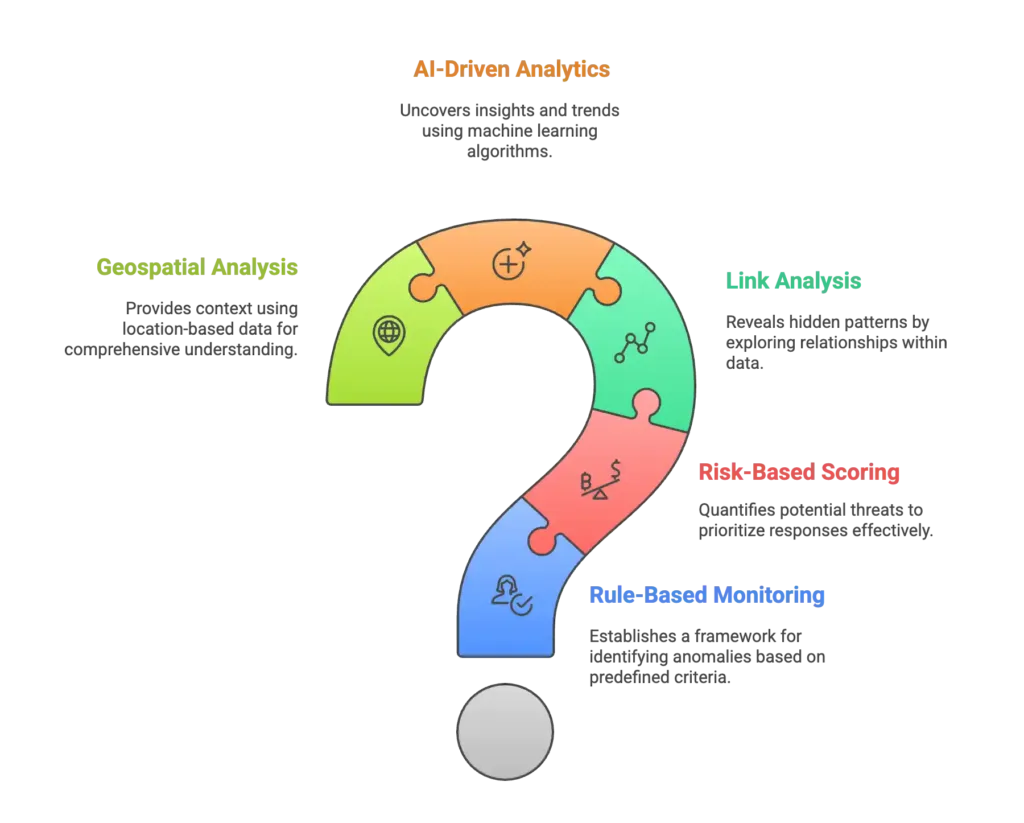
Here are the most widely used approaches:
1) Rule-Based Monitoring
- How it works: Predefined rules flag transactions that breach thresholds (e.g., deposits over $10,000, more than 5 transfers in an hour).
- Strengths: Easy to configure, scalable for large transaction volumes, good for regulatory minimums.
- Limitations: High false positives. A customer’s legitimate activity might trigger alerts if it crosses a set threshold.
2) Risk-Based Scoring
- How it works: Every customer, transaction, or entity is assigned a dynamic risk score based on geography, industry, transaction behaviour, and past patterns.
- Strengths: More nuanced than rules alone; focuses analyst attention on the riskiest cases.
- Limitations: Needs continuous tuning. Without high-quality data, risk scoring can either over-flag or under-flag activity.
3) Link Analysis
- How it works: Connects transactions across accounts, companies, and shell entities to reveal hidden networks.
- Strengths: Helps identify complex laundering schemes like layering or trade-based money laundering (TBML), which would be invisible in isolated transactions.
- Real-world use case: Detecting that multiple companies funnel money to the same offshore director, even though each company looks legitimate in isolation.
4) AI-Driven Analytics
- How it works: Machine learning and anomaly detection models learn from historical cases and adjust as criminals evolve tactics.
- Strengths: Finds patterns beyond human rules, like circular transactions or synthetic IDs. Continuously improves with feedback.
- Example: An AI system flags a small crypto transaction because its flow mirrors a previously identified laundering network.
- Added benefit: Reduces false positives compared to static rules.
5) Geospatial Analysis
- How it works: Monitors the geographic movement of funds, spotting unusual patterns like small transfers spreading across high-risk corridors.
- Strengths: Visual maps highlight hotspots of suspicious activity, useful for cross-border laundering cases.
- Example: Identifying multiple remittances routed through a high-risk jurisdiction in unusual volumes.
Innefu’s Advantage in AML Monitoring
Most anti-money laundering platforms are built to tick compliance checkboxes. They generate alerts, pass them to analysts, and stop there. The problem? This creates noise instead of insight, leaving institutions reactive rather than resilient.
At Innefu Labs, we built Prophecy Eagle I to go beyond monitoring, to act as an intelligence engine.
Entity Resolution
Criminals rarely operate under a single identity. They use aliases, shell companies, and layered ownership structures. Prophecy Eagle I merges fragmented identities across datasets, exposing hidden overlaps between accounts, directors, and transactions.
AI-Driven AML Monitoring
Instead of relying only on static rules, our AI models continuously adapt to new laundering typologies. From crypto wallets to trade-based laundering, the system detects anomalies in real time, minimizing false positives while strengthening detection accuracy.
Link Analysis
Money laundering doesn’t happen in isolation. Prophecy Eagle I visualizes entire laundering webs, showing how individuals, companies, and jurisdictions connect. This allows investigators to target networks, not just single suspicious transfers.
Fusion Capability
Modern laundering often intersects with cybercrime, fraud, and even terrorism financing. Prophecy Eagle I integrates with:
- OSINT feeds to catch online risk signals.
- Cyber forensics for ransomware or phishing-linked funds.
- Defence intelligence for national security–linked threats.
The result: a holistic threat picture, not siloed compliance reports.
On-Premise LLMs
Prophecy Eagle I incorporates air-gapped, secure LLMs that help compliance officers summarize cases, draft Suspicious Activity Reports (SARs), and generate insights, without exposing sensitive data to external systems.
From Compliance to Resilience
With these capabilities, financial institutions shift from reactive compliance (just following the rules) to proactive resilience, anticipating risks, disrupting laundering networks, and protecting the financial ecosystem.
Conclusion – From Monitoring to Mission Readiness
AML transaction monitoring is no longer just about flagging transactions above a threshold. In today’s high-speed financial world, where money moves across borders, cryptocurrencies, and shell entities, static, rule-based systems fall short.
The future lies in platforms that don’t just monitor, they analyze, predict, and connect the dots. By uniting AI-driven monitoring, link analysis, and fusion with cyber and defence intelligence, solutions like Innefu’s Prophecy Eagle I are transforming AML from a compliance burden into a strategic shield for institutions and national security.
FAQ Section
Q1. What is AML transaction monitoring in banking?
AML transaction monitoring refers to the process of analyzing customer transactions in real time to identify suspicious activities linked to money laundering, fraud, or terrorism financing.
Q2. How does AML transaction monitoring work?
It works by combining rule-based alerts, risk scoring, link analysis, and AI-driven analytics to detect unusual transactions and patterns across accounts, networks, and jurisdictions.
Q3. Why is AML transaction monitoring important?
Because it prevents illicit funds from entering the legitimate economy, helps institutions stay compliant with global regulations, and protects against reputational and financial risks.
Q4. What are the challenges in AML transaction monitoring?
The biggest challenge is false positives (legitimate activity flagged as suspicious), which overwhelm compliance teams. Criminals also evolve their tactics, requiring adaptive monitoring systems.
Q5. How does AI improve AML monitoring?
AI reduces false positives, adapts to new laundering techniques, and provides predictive insights by learning from past cases and continuously evolving with new data.
Q6. What makes Innefu’s Prophecy Eagle I different from other AML tools?
Unlike traditional tools, Prophecy Eagle I integrates AI-driven monitoring, entity resolution, link analysis, OSINT, cyber forensics, and on-premise LLMs, transforming compliance into proactive risk intelligence.




