When Mobile Devices Become the Weakest Link in Enterprise Security
In today’s hybrid work culture, mobile devices are no longer secondary tools, they are primary gateways to sensitive enterprise data. Employees check emails on personal phones, access cloud storage on tablets, and join confidential meetings on the go. But with this flexibility comes an often-overlooked villain: the mobile threat.
From spyware to zero-day exploits and malicious apps, the threat landscape has rapidly evolved, and traditional mobile device management (MDM) tools can’t keep up. These attacks are more persistent, more sophisticated, and often invisible until damage is done.
This is where Mobile Threat Defence (MTD) emerges as a comprehensive security framework designed specifically to protect enterprise mobile endpoints, detect anomalous behaviour, and stop threats in real-time.
As organizations increasingly adopt BYOD (Bring Your Own Device) and COPE (Corporate-Owned, Personally Enabled) models, securing every mobile touchpoint has become non-negotiable. The conflict lies in balancing productivity and user privacy while maintaining ironclad security.
In this blog, we’ll break down what MTD really is, why it’s essential, and how your organization can deploy a mobile-first defence strategy that’s proactive, intelligent, and future-ready.
What is Mobile Threat Defence (MTD)?
A Specialized Shield for a Specialized Threat Landscape
Mobile Threat Defence (MTD) is more than a security add-on, it’s a dedicated approach to detecting, preventing, and responding to threats that specifically target mobile devices within an enterprise environment.
As mobile devices become gateways to corporate data, threat actors have adapted. They exploit mobile-specific vulnerabilities: phishing links sent via messaging apps, apps with hidden malware, zero-click exploits that don’t require user interaction, and rogue access points that silently siphon data.
MTD solutions are purpose-built to counter these risks. Unlike traditional MDMs that focus on policy enforcement and device management, Mobile Threat Defence or MTD goes deeper, inspecting behaviour, traffic, system anomalies, and app behaviour in real time.
Core Functions of MTD Solutions:
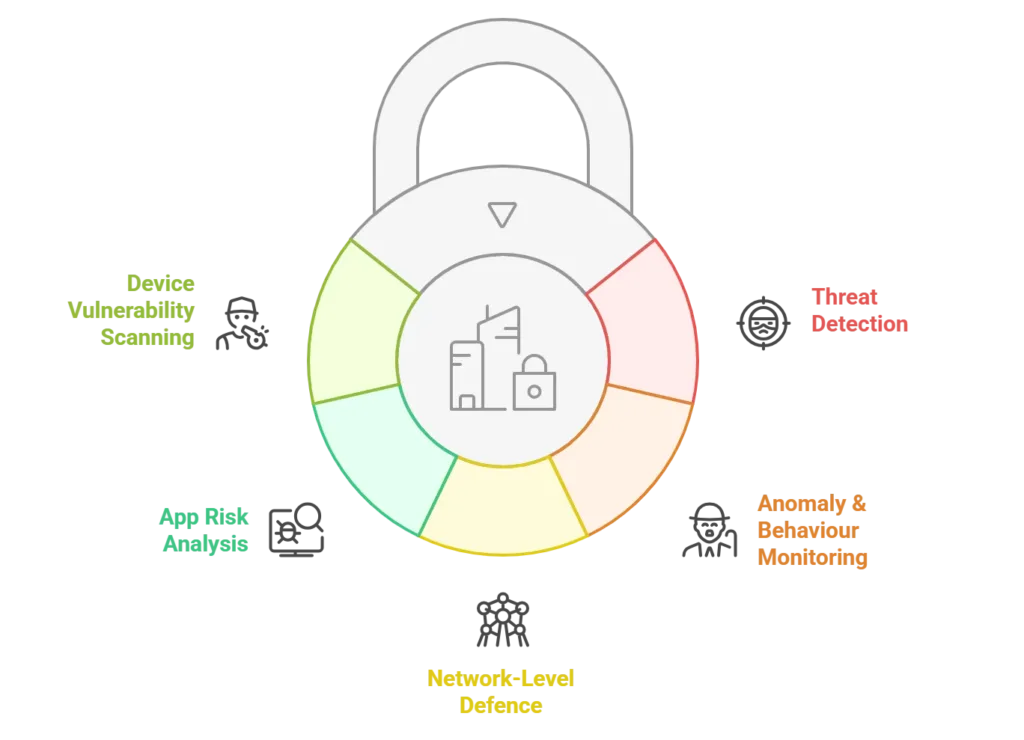
- Threat Detection: Identifying malware, spyware, and riskware on both Android and iOS devices.
- Anomaly & Behaviour Monitoring: Detecting suspicious user or app behaviour that might indicate compromise.
- Network-Level Defence: Preventing man-in-the-middle (MITM) attacks, blocking malicious connections, and securing data-in-transit.
- App Risk Analysis: Scanning app behaviour s and permissions before and after installation.
- Device Vulnerability Scanning: Proactively flagging OS-level vulnerabilities, misconfigurations, and outdated software.
The power of MTD lies in visibility. Security teams gain centralized control over mobile endpoints, with actionable intelligence to isolate threats before they spread, all without infringing on user privacy.
In short, Mobile Threat Defence is not just about stopping known threats but identifying the unknown. It fills the critical gap between mobile flexibility and enterprise-grade cybersecurity, ensuring that the mobile revolution doesn’t become a security liability.
Why Organizations Need MTD Solutions Today
Mobile Devices Are the New Attack Surface. And They’re Being Targeted Relentlessly
The modern workforce is mobile, and so are cyber threats.
As organizations embrace BYOD and COPE policies to drive flexibility and productivity, the number of unmanaged or lightly secured mobile endpoints is exploding. Employees routinely use personal devices to access corporate email, financial apps, CRM systems, and cloud platforms. But every convenience comes with a risk: each mobile device becomes a potential entry point for attackers.
The Shift in the Threat Landscape
Gone are the days when cyberattacks were limited to desktops and servers. Today’s attackers are exploiting mobile-specific vectors like:
- SMS-based phishing (smishing)
- Malicious mobile applications
- Compromised public Wi-Fi networks
- Zero-click spyware infections
- Unpatched operating system vulnerabilities
And unlike traditional endpoints, mobile devices often fly under the radar of centralized security tools, giving attackers a blind spot to exploit.
Why Traditional Security Tools Fall Short
MDM (Mobile Device Management) and UEM (Unified Endpoint Management) tools help enforce policies, but they don’t detect behavioural anomalies, inspect app traffic, or prevent zero-day malware.
This gap is why Mobile Threat Defence (MTD) is no longer optional, it’s essential.
High-Risk Scenarios That Demand MTD:
- BYOD employees accessing sensitive data over unsecured networks
- Executives with elevated permissions vulnerable to targeted spyware
- Remote workforces with decentralized IT oversight
- Industries with compliance mandates (BFSI, healthcare, government)
Key Capabilities of an Effective Mobile Threat Defence Platform
What Makes a Mobile Threat Defence Solution Truly Enterprise-Grade?
Deploying an MTD solution isn’t just about checking a security box, it’s about ensuring your organization has real, layered protection against both known and emerging mobile threats. A capable MTD platform doesn’t rely on signatures alone; it analyzes behaviour, enforces policy, and blocks threats in real time, across all layers of the device experience.
Let’s break down the essential capabilities of a robust Mobile Threat Defence solution:

1. Vulnerability Management
Every unpatched device or misconfigured setting is a welcome sign for attackers.
MTD platforms must:
- Continuously scan for OS and app-level vulnerabilities
- Flag outdated firmware or dangerous configurations
- Provide actionable remediation steps to IT and security teams
Why it matters: Prevents exploitation before attackers can gain a foothold.
2. Anomaly Detection
Behaviour speaks louder than code.
MTD uses AI/ML to detect deviations in:
- Device behaviour (e.g., sudden battery drain, CPU spikes)
- Network usage patterns
- App behaviour and permission changes
Why it matters: Catches threats that bypass traditional signature-based detection, including zero-day attacks.
3. Behavioural Profiling
Instead of reacting after a breach, MTD platforms build profiles of normal device, user, and app behaviour.
This helps:
- Detect insider threats or compromised users
- Identify risky third-party app activity
- Automatically quarantine suspicious devices
Why it matters: Enables real-time detection with minimal false positives.
4. Code Emulation
Before malware executes, MTD platforms can emulate the code in a sandbox environment to observe behaviour.
- Simulates how the code would run on a real device
- Identifies intent (e.g., keylogging, data exfiltration)
- Stops execution proactively
Why it matters: Neutralizes threats before they reach the user.
5. Intrusion Prevention
Attackers often enter through unsecured networks and rogue connections.
Effective MTD should:
- Block malicious URLs and phishing domains
- Detect and prevent MITM (Man-in-the-Middle) attacks
- Restrict access from compromised Wi-Fi or VPN tunnels
Why it matters: Secures the mobile network layer, often the first point of compromise.
6. Host Firewalling
Not all threats come from the outside.
MTD adds host-level firewalling to:
- Control incoming/outgoing network access
- Prevent unauthorized lateral movement inside the enterprise
- Enforce granular access control at the device level
Why it matters: Limits the blast radius in case of a breach.
7. Transport Security
Data in motion is a prime target for interception.
MTD solutions enforce:
- End-to-end encryption (TLS/SSL)
- VPN tunnelling policies for sensitive data access
- Detection of insecure data transmission channels
Why it matters: Ensures enterprise data remains confidential, even on public or untrusted networks.
Together, these capabilities form the backbone of a modern, resilient mobile security posture. It’s not enough to simply monitor devices, organizations need MTD platforms that actively detect, decide, and defend at the speed of threat evolution.
Protecting BYOD and COPE Devices in the Enterprise
Balancing Productivity, Privacy, and Protection
When employees use their own smartphones to check emails, join meetings, or access internal files, the line between personal and corporate security becomes dangerously thin.
Modern enterprises commonly operate under two models:
- BYOD (Bring Your Own Device): Employees use their personal devices for work.
- COPE (Corporate-Owned, Personally Enabled): Companies provide the devices but allow personal use.
While both increase flexibility and reduce hardware costs, they also introduce fragmented control and high-risk exposure. This is where the conflict arises: How do you secure enterprise data without infringing on personal privacy or user experience?
The Challenge with BYOD and COPE Devices
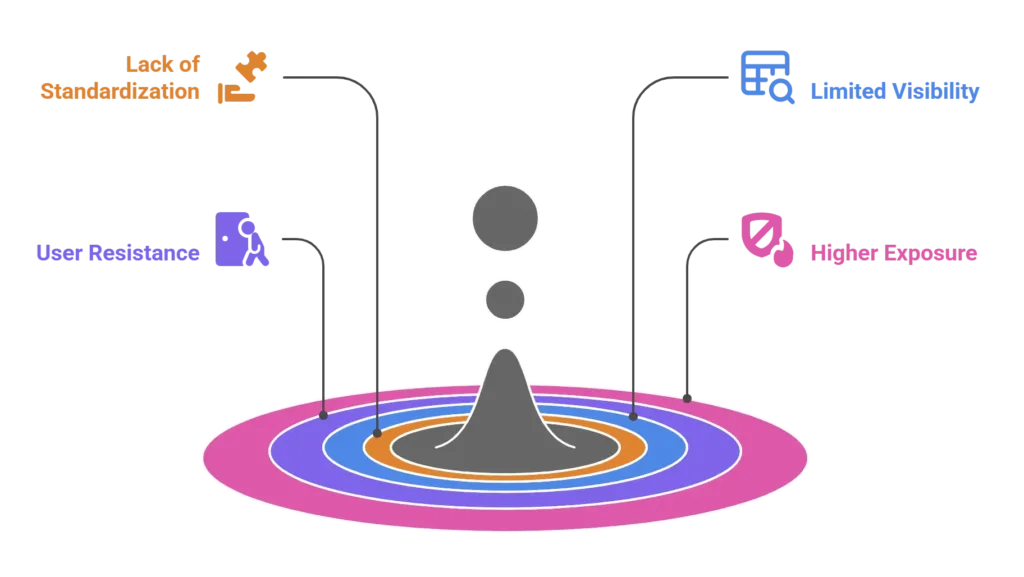
- Lack of standardization across operating systems, apps, and security posture
- Limited visibility for IT teams into potential threats on personal devices
- User resistance to invasive security controls on their own phones
- Higher exposure to unsecured networks and rogue applications
Traditional MDM solutions often hit a wall here, they’re either too invasive, risking user backlash, or too lenient, leaving critical gaps.
How MTD Bridges the Gap
Mobile Threat Defence platforms are built to secure BYOD and COPE devices without compromising user autonomy. They offer:
- Non-intrusive monitoring: Behaviour al and threat detection without personal data access
- Privacy-respecting controls: MTD solutions operate within privacy guidelines, avoiding collection of personal content like photos, messages, or call logs
- Automated policy enforcement: Devices that fall out of compliance (e.g., jailbroken, outdated OS) can be flagged or quarantined automatically
- Flexible integration with MDM/UEM tools: Ensuring seamless policy coordination across device fleets
Empowering Security Teams and End Users
For CISOs and IT teams, MTD delivers detailed compliance and risk posture reports. For users, it ensures their devices are safe, not just for work but in everyday use.
The takeaway? MTD doesn’t just protect enterprise data. It empowers employees to work securely on any device, anywhere, without friction.
In a mobile-first world, trust must be built into every endpoint, and Mobile Threat Defence ensures that trust is verified, not assumed.
Real-Time Mobile Device Monitoring
Because Threats Don’t Wait, And Neither Should Your Defences
Mobile threats don’t operate on a schedule; they strike when you least expect. From rogue access points during airport layovers to malicious app behaviour triggered after installation, mobile devices are exposed to dynamic, fast-moving threats that demand an always-on, intelligent monitoring approach.
This is where real-time mobile device monitoring becomes essential, a defining capability of any serious Mobile Threat Defence (MTD) solution.
Beyond Periodic Scanning: Continuous Visibility
Traditional security approaches often rely on scheduled scans or reactive logging. But mobile threats evolve too quickly for that. MTD solutions enable:
- Continuous behaviour analysis at the device, network, and application levels
- Instant alerts on anomalous activity, compromised configurations, or policy violations
- Real-time remediation such as quarantining the device, blocking access, or auto-removing malicious apps
The key value: Mobile threats are intercepted before they impact the enterprise, not after.
Centralized Dashboards for Enterprise-Grade Oversight
Security teams need more than alerts, they need clarity. MTD platforms provide:
- Unified dashboards showing the health status of all enrolled devices
- Risk scoring per user, device, and app
- Audit trails and threat intelligence for incident response
- Integration with SIEM, SOAR, and EDR systems for holistic visibility across the enterprise security fabric
Automation Meets Intelligence
Real-time doesn’t mean noisy. Advanced MTD tools use AI/ML to filter false positives, prioritize threats, and trigger automated playbooks, ensuring that your security operations remain lean, effective, and fast.
In a world where mobile endpoints are both assets and liabilities, real-time monitoring isn’t just a feature, it’s your first line of defence against compromise.
Final Thoughts
Mobile Security Is No Longer Optional, It’s Mission-Critical
In an era where work happens everywhere, in airports, cafes, home offices, and across borders, mobile devices are the most used yet least protected enterprise endpoints. The threat landscape has evolved, and attackers know exactly where the gaps are. The question is: has your organization evolved its defences accordingly?
Mobile Threat Defence (MTD) is not just another security tool. It’s a strategic enabler, one that empowers businesses to embrace mobility without compromising security, privacy, or compliance. From anomaly detection and code emulation to real-time monitoring and behaviour al profiling, MTD platforms deliver the depth of protection traditional tools simply can’t offer.
Organizations that continue to rely on outdated approaches or stopgap measures are leaving themselves exposed, not just to malware or spyware, but to data breaches, compliance failures, reputational loss, and operational disruption.
The Next Step? Act Before You’re Forced To
If mobile is now central to how your workforce operates, MTD must be central to how you defend. Secure your mobile ecosystem now, before it becomes your weakest link.
Explore enterprise-grade Mobile Threat Defence solutions: Request a Demo from the Mobile Threat Defence Experts!
FAQs
- What is Mobile Threat Defence (MTD)?
Mobile Threat Defence (MTD) is a security solution that detects, prevents, and responds to mobile-specific threats such as malware, spyware, phishing, and network attacks. - Why is MTD important for enterprise mobile security?
MTD provides real-time protection against mobile threats, especially in BYOD and COPE environments where traditional security tools fall short. - How does Mobile Threat Defence work?
MTD works by continuously analyzing device behaviour, detecting anomalies, scanning apps, securing network traffic, and blocking malicious activity. - What are the key features of a Mobile Threat Defence solution?
Top MTD features include vulnerability management, anomaly detection, behaviour al profiling, intrusion prevention, host firewalling, and transport layer security. - Is MTD required for BYOD and COPE environments?
Yes, MTD is essential for securing both BYOD and COPE devices as they increase exposure to mobile threats outside corporate-controlled networks. - What’s the difference between MDM and MTD?
MDM (Mobile Device Management) focuses on policy control and configuration, while MTD provides deep threat detection and real-time protection against mobile attacks. - How does MTD protect against spyware like Pegasus?
Advanced MTD platforms detect behaviours linked to spyware like Pegasus, including zero-click exploits, unusual data transfers, and system-level manipulations. - Can MTD detect zero-day mobile threats?
Yes, modern MTD solutions use behaviour al analysis and machine learning to detect unknown or zero-day threats based on activity patterns. - Does MTD affect user privacy on personal devices?
No, enterprise-grade MTD platforms are designed to respect privacy, monitoring only work-related activity without accessing personal data like photos or messages. - How can I choose the right MTD solution for my organization?
Look for MTD solutions with real-time detection, seamless MDM integration, compliance reporting, and support for both Android and iOS platforms.




